- Homepage /
- Blog /
-
Digital Trust 2030: How AI and Cybersecurity Will Redefine Safety in the Digital Age
Digital Trust 2030: How AI and Cybersecurity Will Redefine Safety in the Digital Age

Digital Trust 2030: How AI and Cybersecurity Will Redefine Safety in the Digital Age
Introduction
Trust has always been the foundation of human relationships — and now it is becoming the foundation of the digital economy. In a world where artificial intelligence (AI) can generate convincing deepfakes, quantum computers threaten current encryption, and cyberattacks are launched by autonomous bots, the question is no longer if we can be hacked but when and how often.
By 2030, digital trust will be the most valuable asset for organizations, governments, and individuals alike. Cybersecurity will move from a defensive necessity to the very core of strategic leadership. This article explores the future of AI-driven cyber defense, deepfake manipulation, Zero Trust 2.0, quantum-safe encryption, and the cultural shifts that will decide who thrives — and who disappears — in the digital age.
1. AI as a Weapon and a Shield
Artificial intelligence is both the greatest threat and the greatest hope for cybersecurity.
AI-powered attacks
- Phishing at scale: LLMs generate hyper-personalized emails indistinguishable from real communication.
- Deepfake fraud: AI creates audio or video impersonations of CEOs, politicians, or family members.
- Autonomous malware: Self-learning malicious code that adapts to security defenses in real time.
AI-powered defense
- Anomaly detection: Systems that identify subtle irregularities in network traffic.
- Predictive intelligence: Forecasting attacks before they occur, based on historical and real-time data.
- Automated response: Isolating compromised devices instantly without human intervention.
The battlefield of the future will be AI vs. AI, and the smarter algorithm will win.
2. The Deepfake Economy
By 2030, deepfakes will move far beyond entertainment. They will challenge the very notion of truth.
- Business risks: Fraudulent calls or video conferences trick employees into transferring millions.
- Political manipulation: Fake speeches or fabricated evidence destabilize elections.
- Personal harm: Identity theft and reputational damage through falsified media.
To counter this, companies and governments will rely on deepfake detection AI, digital watermarking, and proof-of-authenticity systems embedded in every communication channel. The fight for truth will be as important as the fight for security.
3. Zero Trust 2.0
The classic Zero Trust model — “never trust, always verify” — is evolving.
Future principles of Zero Trust 2.0:
- Continuous identity validation: Biometric, behavioral, and contextual authentication at every step.
- Micro-segmentation of networks: Every device, app, and service operates within isolated compartments.
- AI-driven adaptive trust: Systems that adjust access dynamically based on real-time risk analysis.
By 2030, Zero Trust 2.0 will be the global standard, embedded in every cloud platform, IoT network, and enterprise system.
4. Quantum-Safe Internet
Quantum computing represents both innovation and disruption. Once quantum machines become powerful enough, they could break today’s most widely used encryption methods within minutes.
Preparing for the “Q-Day”
- Post-quantum cryptography (PQC): Algorithms resistant to quantum attacks, standardized by organizations like NIST.
- Quantum key distribution (QKD): Using the laws of physics to secure communication with unbreakable keys.
- Hybrid encryption models: Combining classical and quantum-safe protocols during the transition period.
By the end of the decade, governments and enterprises will be forced to migrate to quantum-resistant infrastructure — those who delay risk catastrophic breaches.
5. Digital Identity and Authentication
Proving who you are will be the central challenge of the digital era.
Key trends:
- Biometric evolution: Beyond fingerprints and face scans — continuous monitoring of behavioral patterns.
- Blockchain-based identities: Decentralized systems that allow individuals to control their own digital identity.
- Reputation scoring: Devices and users gain “trust scores” based on behavior, much like credit ratings.
In 2030, identity will no longer be a static credential. It will be a dynamic profile, constantly updated and verified in real time.
6. Culture and Education: The Human Factor
Technology alone cannot secure the future. People remain the weakest link, exploited through phishing, social engineering, and manipulation.
Organizations must invest in:
- Continuous awareness programs — not once a year, but every week.
- Gamified training to make security engaging.
- Shared responsibility culture where every employee becomes part of the defense.
Cybersecurity in 2030 will be less about firewalls and more about mindsets. Companies with a strong security culture will prove far more resilient than those relying only on advanced tools.
7. Geopolitics and Cyber Conflicts
Cybersecurity is no longer limited to corporations — it has become a matter of global security.
- Cyber warfare: States deploying AI-driven attacks to paralyze infrastructure.
- Cyber espionage: Targeting intellectual property, trade secrets, and government intelligence.
- Digital alliances: Countries forming cyber defense treaties, much like NATO, to combat transnational threats.
The digital battlefield will shape geopolitics as much as physical territories. Nations that fail to secure their digital infrastructure risk losing sovereignty.
8. Cybersecurity as a Business Strategy
Cybersecurity is no longer a cost — it is a competitive advantage.
- Trust as a currency: Companies with proven digital security will attract more customers.
- Investor confidence: ESG and risk assessments now include cybersecurity resilience.
- Brand protection: A single breach can destroy years of reputation.
By 2030, digital trust will define market leaders. Businesses that embed security into their DNA will win; those that treat it as an afterthought will vanish.
9. Scenarios for 2030
Optimistic scenario
AI-driven defenses, quantum-safe internet, and strong regulations create a world where digital trust is universal. Cybercrime exists but is manageable, and most interactions are safe.
Realistic scenario
Cybersecurity becomes a constant arms race. Organizations invest heavily in AI, but so do attackers. Breaches happen regularly, but damage is contained through resilience and recovery.
Pessimistic scenario
Quantum breakthroughs outpace defenses, deepfakes destroy trust in media, and cyber conflicts escalate. Trust collapses, leading to economic and political instability.
Which path we take will depend on global collaboration and early investment.
Conclusion
By 2030, cybersecurity will no longer be about defending networks — it will be about preserving trust in every interaction. In a world of AI-generated deception and quantum-powered threats, the ability to prove authenticity, secure data, and build resilient cultures will define survival.
The future belongs to those who treat digital trust as their most important asset. Organizations that embed AI-driven security, adopt Zero Trust 2.0, migrate to quantum-safe infrastructure, and foster strong security cultures will thrive.
Those who hesitate may discover that in the digital economy, trust is not just a value — it is the currency of survival.
Przeglądaj inne artykuły

Liquidity Is Not Volume: The Structural Mistake That Kills Marketplaces

The Take Rate Trap: Why Raising Commissions Is the Fastest Way to Kill a Marketplace

When to Fire Sellers: Why the Best Marketplaces Grow Faster by Shrinking Supply

Marketplace Support Costs: The Hidden Margin Killer No One Models
Tiered Pricing Without Backlash: How to Monetize Sellers Without Killing Growth

Seller Segmentation: The Missing System Behind Profitable Marketplaces

Why Most Marketplaces Die at €1–3M GMV (And How to Avoid It)
Marketplace Unit Economics: When Growth Actually Becomes Profitable
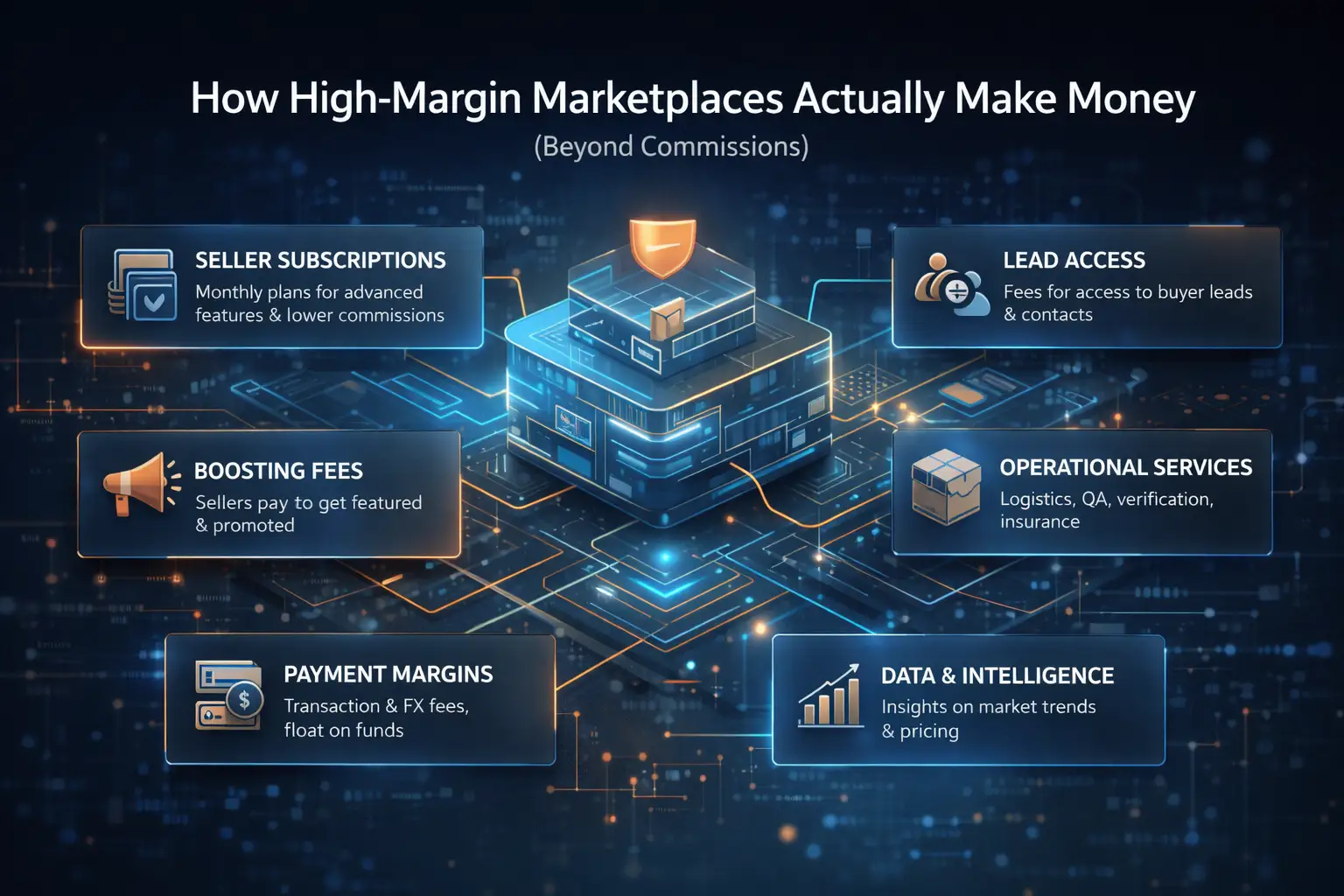
How High-Margin Marketplaces Actually Make Money (Beyond Commissions)

Algorithmic Middle Management: How Software Replaces Control Layers

The Rise of Internal Software: Why the Most Profitable Digital Products Are Built for Companies, Not

Decision-Centric Software: Why the Real Value of Digital Products Is Shifting from Features to Decis

Software That Never Launches: Why Continuous Evolution Is Replacing Releases and Roadmaps

Digital Products Without Users: When Software Works Entirely Machine-to-Machine

Unbundled Platforms: Why the Future of Digital Products Belongs to Ecosystems, Not Single Applicatio

Silent Software: Why the Most Valuable Digital Products of the Future Will Be the Ones Users Barely

Cognitive Commerce: How AI Learns to Think Like Your Customers and Redefines Digital Shopping

Predictive UX: How AI Anticipates User Behavior Before It Happens

AI-Driven Product Innovation: How Intelligent Systems Are Transforming the Way Digital Products Are

Adaptive Commerce: How AI-Driven Systems Automatically Optimize Online Stores in Real Time

Zero-UI Commerce: How Invisible Interfaces Are Becoming the Future of Online Shopping

AI Merchandising: How Intelligent Algorithms Are Transforming Product Discovery in Modern E-Commerce

Composable Commerce: How Modular Architecture Is Reshaping Modern E-Commerce and Marketplace Develop

Context-Aware Software: How Apps Are Becoming Smarter, Adaptive, and Environment-Responsive

AI-Driven Observability: The New Backbone of Modern Software Systems

Hyper-Personalized Software: How AI Is Creating Products That Adapt Themselves to Every User

Edge Intelligence: The Future of Smart, Decentralized Computing

AI-Powered Cybersecurity: How Intelligent Systems Are Redefining Digital Defense

Modern Software: How Our Company Is Reshaping the Technology Landscape

From Digital Transformation to Digital Maturity: Building the Next Generation of Tech-Driven Busines

AI Agents: The Rise of Autonomous Digital Workers in Business and Software Engineering

Synthetic Data: The Next Frontier of AI and Business Intelligence

Quantum AI: How Quantum Computing Will Redefine Artificial Intelligence and Software Engineering

Design Intelligence: How AI Is Redefining UX/UI and Digital Product Creativity

How Artificial Intelligence Is Transforming DevOps and IT Infrastructure

AI Observability in Production: Monitoring, Anomaly Detection, and Feedback Loops for Smart Applicat

Low-Code Revolution: How Visual Development Is Transforming Software and Marketplace Creation

Composable Marketplaces: How Modular Architecture Is the Future of Platform Engineering

AI-Powered Storyselling: How Artificial Intelligence Is Reinventing Brand Narratives

The Era of Invisible Commerce: How AI Will Make Shopping Disappear by 2030

From Attention to Intention: The New Era of E-Commerce Engagement

Predictive Commerce: How AI Can Anticipate What Your Customers Will Buy Next

Cybersecurity in the Age of AI: Protecting Digital Trust in 2025–2030

The Future of Work: Humans and AI as Teammates

Green IT: How the Tech Industry Must Adapt for a Sustainable Future

Emerging Technologies in IT: What Will Shape 2025–2030
Growth Marketing – A Fast-Track Strategy for Modern Businesses

AI SEO Tools – 5 Technologies Revolutionizing Online Stores

AI SEO – How Artificial Intelligence Is Transforming Online Store Optimization

Product-Led Growth – When the Product Sells Itself

Technology in IT – Trends Shaping the Future of Business and Everyday Life

Marketplace Growth – How Exchange Platforms and E-commerce Build the Network Effect

Edge Computing – Bringing Processing Power Closer to the User

Agentic AI in Applications – When Software Starts Acting on Its Own

Neuromorphic Computers and 6G Networks – The Future of IT That Will Change the Game

Meta Llama 3.2 – The Open AI That Could Transform E-Commerce and SEO

AI Chatbot for Online Stores and Apps – More Sales, Better SEO, and Happier Customers

5 steps to a successful software implementation in your company

Innovative IT solutions — why invest now?

Innovative software development methods for your business

5 steps to successfully implement technological innovation in your company
